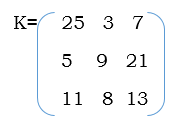NOTE!
Click on MENU to Browse between Subjects...17CS61 - CRYPTOGRAPHY, NETWORK SECURITY AND CYBER LAW
6TH SEMESTER ISE & CSE
Answer Script for Module 1
Solved Previous Year Question Paper
CBCS SCHEME
CRYPTOGRAPHY, NETWORK SECURITY AND CYBER LAW
[As per Choice Based Credit System (CBCS) scheme]
(Effective from the academic year 2017 - 2018)
SEMESTER - VI
Subject Code 17CS61
IA Marks 40
Number of Lecture Hours/Week 3
Exam Marks 60
These Questions are being framed for helping the students in the "FINAL Exams" Only
(Remember for Internals the Question Paper is set by your respective teachers).
Questions may be repeated, just to show students how VTU can frame Questions.
- ADMIN
17CS61 - CRYPTOGRAPHY, NETWORK SECURITY AND CYBER LAW
6TH SEMESTER ISE & CSE
Answer Script for Module 1
1.1 Cyber Attack:
cyberattack is any type of offensive maneuver that targets computer information systems, infrastructures, computer networks, or personal computer devices. An attacker is a person or process that attempts to access data, functions or other restricted areas of the system without authorization, potentially with malicious intent. Depending on context, cyberattacks can be part of cyberwarfare or cyberterrorism . A cyberattack can be employed by sovereign states , individuals, groups, society or organizations, and it may originate from an anonymous source.
A cyberattack may steal, alter, or destroy a specified target by hacking into a susceptible system. Cyberattacks can range from installing spyware on a personal computer to attempting to destroy the infrastructure of entire nations. Legal experts are seeking to limit the use of the term to incidents causing physical damage, distinguishing it from the more routine data breaches and broader hacking activities.
1.2 Motives of Cyber Attacks:
The sheer thrill of mounting a successful cyber-attack has been motivation enough for hackers (Table 1.1)
|
Year |
Event |
|
1988 |
Robert Morrisa 23-year-old Cornell graduate student, released a worm that over an Arpanet, incapacitating almost 6000 computers, congesting government and university systems. He was fined $10,000 and sentenced to 3 years' probation. |
|
1991 |
31-year-old David L. Smith created the worm "Melissa," which infected thousands of computers causing damage of approximately $1.5 billion. This virus sent copies of itself to the first 50 names of the recipient's address book. He received a 20-month jail term. |
|
2001 |
"Anna Kournikova" virus. Promising photos of the tennis star mailed itself to the every person in the victim's address book. Investigators were apprehensive that the virus was created with a toolkit enabling the rookies to create a virus. |
|
2008 |
The headquarters of the Obama and McCain presidential campaigns were hacked. |
Table 1.1 Notable cyber attacks
Most hackers were (and still are) young adults, often teens, who had dropped out of school but were otherwise intelligent and focused. Many of the "traditional" hackers seem to be obsessive programmers. They seem to be adept at circumventing limitations to achieve a challenging but often forbidden objective.
In addition, there is a tribe of script kiddies - juveniles who use scripts and attack kits designed by others (these can be freely downloaded from the Internet). Their activities do not require any special programming skills or advanced knowledge of computer systems.
Other perpetrators of cyber-attacks include company insiders, often disgruntled employees who. wish to even scores with their employers. There is also a serious threat from cyber terrorists who espouse extreme religious or political causes. Cyber terrorism is one weapon in their impressive arsenal which may include biological, chemical, and nuclear weapons. Their goals are to cripple the information/communication systems of the financial and business institutions of their "enemies."
Some of the main motives of launching cyber-attacks are:
1. Theft of sensitive information.
2. Disruption of service.
3. Illegal access to or use of resources
1.2.1 Theft of sensitive information.
i. Many organizations store and communicate sensitive information.
ii. Information on new products being designed or revenue sources can be hugely advantageous to a company's competitors.
iii. Likewise, details of military installations or precise military plans can be of immense value to a nation's adversaries.
iv. Political spying targeted at government ministries and national intelligence can HAVE many sensitive operations planned for the future.
v. Besides corporations, banks, the military, intelligence, etc., the individual too has increasingly been a target.
vi. Leakage of personal information such as credit card numbers, passwords, and even personal spending habits are common and are collectively referred to as identity theft. Such information is advertised on certain websites and may be purchased for a small fee.
1.2.2 Disruption of service.
i. Interruption or disruption of service is launched against an organization's servers so they are made unavailable or inaccessible.
ii. In recent times, there have been unconfirmed reports of such attacks being launched by business rivals of e-commerce websites.
iii. The goal here appears to be "my competitor's loss is my gain." In 2001, there were a series of such attacks that targeted the websites of Yahoo, Microsoft, etc. in a short span of time.
iv. They were meant to alert corporates and others of the dangers of this class of attacks.
1.2.3 Illegal access to or use of resources
i. The goal here is to obtain free access or service to paid services.
ii. Examples of this include free access to online digital products such as magazine or journal articles, free talk time on someone else's account, free use of computing power on a supercomputer, etc.
iii. In each case, the attacker is able to circumvent controls that permit access to only paid subscribers of such services.
2.1 Extended Euclidean Algorithm:
The formal procedure to obtain the inverse of c modulo b is called the Extended Euclidean Algorithm and ts presented next. It assumes that b and c are relatively prime.
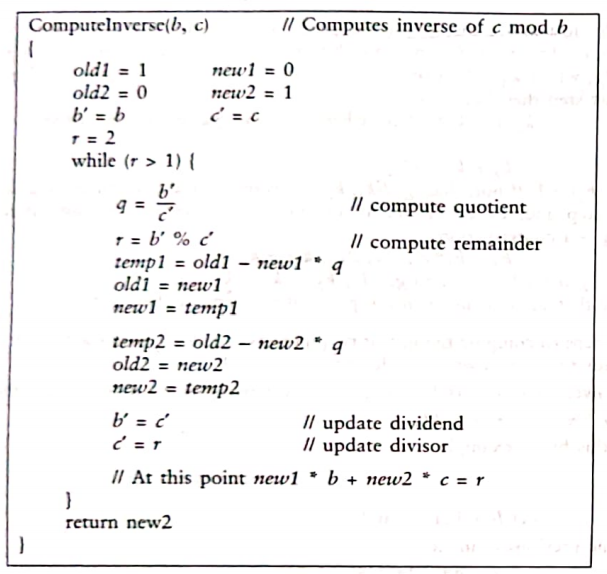
Fig 2.1: Extended Euclidean Algorithm
2.2 We use the Extended Euclidean Algorithm (Fig. 2.1) to compute the
inverse of 12 modulo 79 (b = 79 and c = 12)
Table 2.2 tracks the values of b’, c’, q, r, old1, new1, old2, and new2 at the end of each iteration. The invariant, new1 x b + new2 x c = r is maintained across all iterations. At the end of the last iteration r = 1 and the invariant is
(-5) x 79 + 33 x 12 =1,
or
12 * 33 = 1+5 * 79 = 1 (mod 79)
Thus, the inverse of 12 modulo 79 is 33.
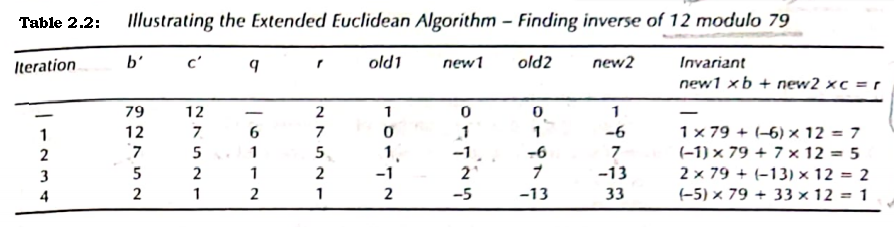
Table 2.2: Illustrating the Extended Euclidean Algorithm - Finding inverse of 12 modulo 79
The Vigenere cipher
is a polyalphabetic
that uses a multi-digit cipher key, k1, k2, …, km,
Here, k1, k2, …, km, are each
integer. The plaintext
is split into non-overlapping
blocks, each containing m consecutive characters
. Then thefirst letter
of each block is replaced by the letter k1,
positions to its right, the second letter
of each block is replaced by the letter k2
,
positions to its right, and so on.

The first letter in the above text is W. The corresponding key is 04. This means that the cipher text is the letter 4 positions ahead (in the modulo 26 sense).
The key length = 8, i.e., the key string repeats after every 8 characters.
There are four occurrences of the letter "s" in the above text (for simplicity we do not distinguish between upper and lower case letters). However, each occurrence of "s" is encrypted as a different character in the cipher text - "V", "X", "O" and "Z".
There are at least tour important vulnerability classes in the domain of security:
5.1 Human Vulnerabilities:
These are vulnerabilities caused by human behaviour or action.
For example, the user clicks on a link in an e-mail message received from a
questionable source. By so doing, the user can be directed to a site
controlled by the attacker as in a phishing attack or a cross-site scripting attack
.
Similarly clicking on an e-mail attachment may open up a document causing a macro
to be executed.
The macro may be designed to infect other files
on the
system and/or spread the infected e-mail to other e-mail addresses
harvested from the victim's inbox.
In both these cases, thehuman vulnerability consists of clicking on a link or
attachment in an e-mail from a possibly unknown source.
The link or attachment
may have provoked the victim by a
flashy message suggesting quick money, etc., blinding him/her to the fact
that the message came from an unknown source.
It is actions like this that make a phishing attack or an e-mail virus so very successful.
5.2 Protocol Vulnerabilities:
A number of networking protocols including TCP, IP, ARP, ICMP, UDP, DNS
, and various protocols used
in local area networks (LANs) have features that have been used in
unanticipated ways to craft assorted attacks.
Pharming attacks and various hijacking attacks
are some examples.
There are tools availableon-line to facilitate some of these attacks.
One such tool subverts the normal functioning of the ARP protocol to sniff passwords from a LAN.
There are a number of vulnerabilities in thedesign of security protocols
that lead to replay or man-in-the-middle attacks.
These attacks, in turn, lead to identity theft, compromise of secret keys, etc.
Vulnerabilities in network protocols are often related to aspects of their design though they may also be the result of poor implementation or improper deployment.
5.3 Software Vulnerabilities:
This family of vulnerabilities is caused by written system or application software.
In many cases, the causes of the problem seem to be the code that is all too trusting of user input.
Ex A web server accepts input from a user's browser. the web server must accept the request after typing the complete username and password. the server software should perform sufficient validation.
5.4
Configuration Vulnerabilities:
These relate to configuration settings on newly installed applications, files, etc.
Read-write-execute
permissions on files may be too generous and susceptible to
abuse.
The privilege level assigned to a process may be higher than what it should be to carry out a task. This privilege may be misused during some point in its execution leading to what are commonly called "privilege escalation" attacks.
Besides misconfiguration of software and services, security appliances such as firewalls may be incorrectly or incompletely configured with possibly devastating effect.
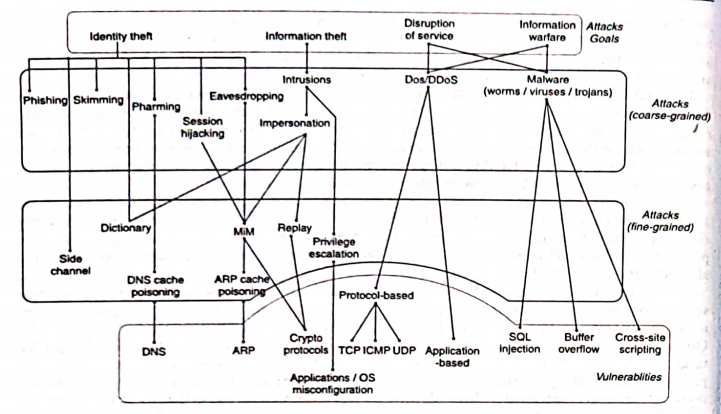
Fig 5.1: Common attacks and vulnerabilities
Below Page NAVIGATION Links are Provided...
All the Questions on Question Bank Is SOLVED

 MENU
MENU