CRYPTOGRAPHY, NETWORK SECURITY AND CYBER LAW
[As per Choice Based Credit System (CBCS) scheme]
(Effective from the academic year 2017 - 2018)
SEMESTER - VI
Subject Code 17CS61
IA Marks 40
Number of Lecture Hours/Week 4
Exam Marks 60
CRYPTOGRAPHY, NETWORK SECURITY AND CYBER LAW
Important Questions - MODULE - 1
These Questions are being framed for helping the students in the "FINAL Exams" Only (Remember for Internals the Question Paper is set by your respective teachers). Questions may be repeated, just to show students how VTU can frame Questions.
- ADMIN
17CS61 - CRYPTOGRAPHY, NETWORK SECURITY AND CYBER LAW
Important Questions - MODULE - 1
1. What do you mean by cyber-attack? List and explain main motives of launching cyber-attacks. (8-Marks) (Dec.2019/Jan.2020)
2. Using Extended Euclidean Algorithm find the inverse of 12 modulo 79. (8-Marks) (Dec.2019/Jan.2020)
3. Design known plain test attack to obtain the key used in the Vigenere cipher. (8-Marks) (Dec.2019/Jan.2020)
4. Consider a Hill cipher m = 3 (block size = 3) with key k shown below:
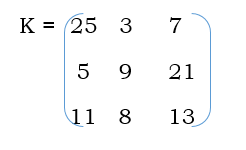
i. What is the cipher text corresponding to the plaintext = (VOW)?
ii. What is the plain text corresponding to the cipher text = (TQX)? (8-Marks) (Dec.2019/Jan.2020)
5. Describe the types of Vulnerabilities to domain of security. (4-Marks) (June/July.2019)
6. List the guiding principles of security. (4-Marks) (June/July.2019)
7. Write the extended Euclidean algorithm, with an example. (8-Marks) (June/July.2019)
8. Calculate the value of x using Chinese remainder theorem by given below data:
N=210, n1 = 5, n2 = 5, n3 = 7, x 1 = 3, x2 = 5, x3 = 2. (5-Marks) (June/July.2019)
9. Explain the Vigenere Cipher and the Hill Cipher techniques with illustration. (6-Marks) (June/July.2019)
10. With neat diagram, explain Fiestel structure. (5-Marks) (June/July.2019)
11. Define cyber security? Explain the motives of cyber-attack. (5-Marks) (DEC 2018/JAN 2019)
12. Use extended Euclidean algorithm to find inverse of 12 modulo 79? (5-Marks) (DEC 2018/JAN 2019)
13. Apply Chinese remainder theorem to find square roots of 3 modulo 143 and list all square roots of -3 modulo 143. (6-Marks) (DEC 2018/JAN 2019)
14. Explain DES construction in detail. (5-Marks) (DEC 2018/JAN 2019)
15. Explain confusion and Diffusion with example. (5-Marks) (DEC 2018/JAN 2019)
16. Explain three sounds SPN Network. (6-Marks) (DEC 2018/JAN 2019)
17. List and explain the various types of vulnerabilities with common cyber-attacks. (8-Marks) (June/July 2018)
18. Encrypt the plaintext "CRYPTOGRAPHY" using hill cipher technique with key matrix. (8-Marks) (June/July 2018)
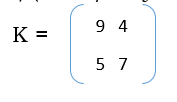
19. Distinguish between:
I. Confusion and diffusion ciphers
II. Block cipher and stream ciphers. (8-Marks) (June/July 2018)
20. with a neat schematic, explain the single round of DES encryption model. (8-Marks) (June/July 2018)
-ADMIN
ANSWER SCRIP FOR THESE QUESTIONS WILL BE UPLOADED "AS SOON AS POSSIBLE"
Visit: https://hemanthrajhemu.github.io/AnswerScript/
For immediate Notification Join the Telegram Channel
-ADMIN
T = Text book
QB = Question Bank
AS = Amswer Script
-ADMIN

 MENU
MENU

